- Topic1/3
8k Popularity
27k Popularity
11k Popularity
5k Popularity
173k Popularity
- Pin
- Hey fam—did you join yesterday’s [Show Your Alpha Points] event? Still not sure how to post your screenshot? No worries, here’s a super easy guide to help you win your share of the $200 mystery box prize!
📸 posting guide:
1️⃣ Open app and tap your [Avatar] on the homepage
2️⃣ Go to [Alpha Points] in the sidebar
3️⃣ You’ll see your latest points and airdrop status on this page!
👇 Step-by-step images attached—save it for later so you can post anytime!
🎁 Post your screenshot now with #ShowMyAlphaPoints# for a chance to win a share of $200 in prizes!
⚡ Airdrop reminder: Gate Alpha ES airdrop is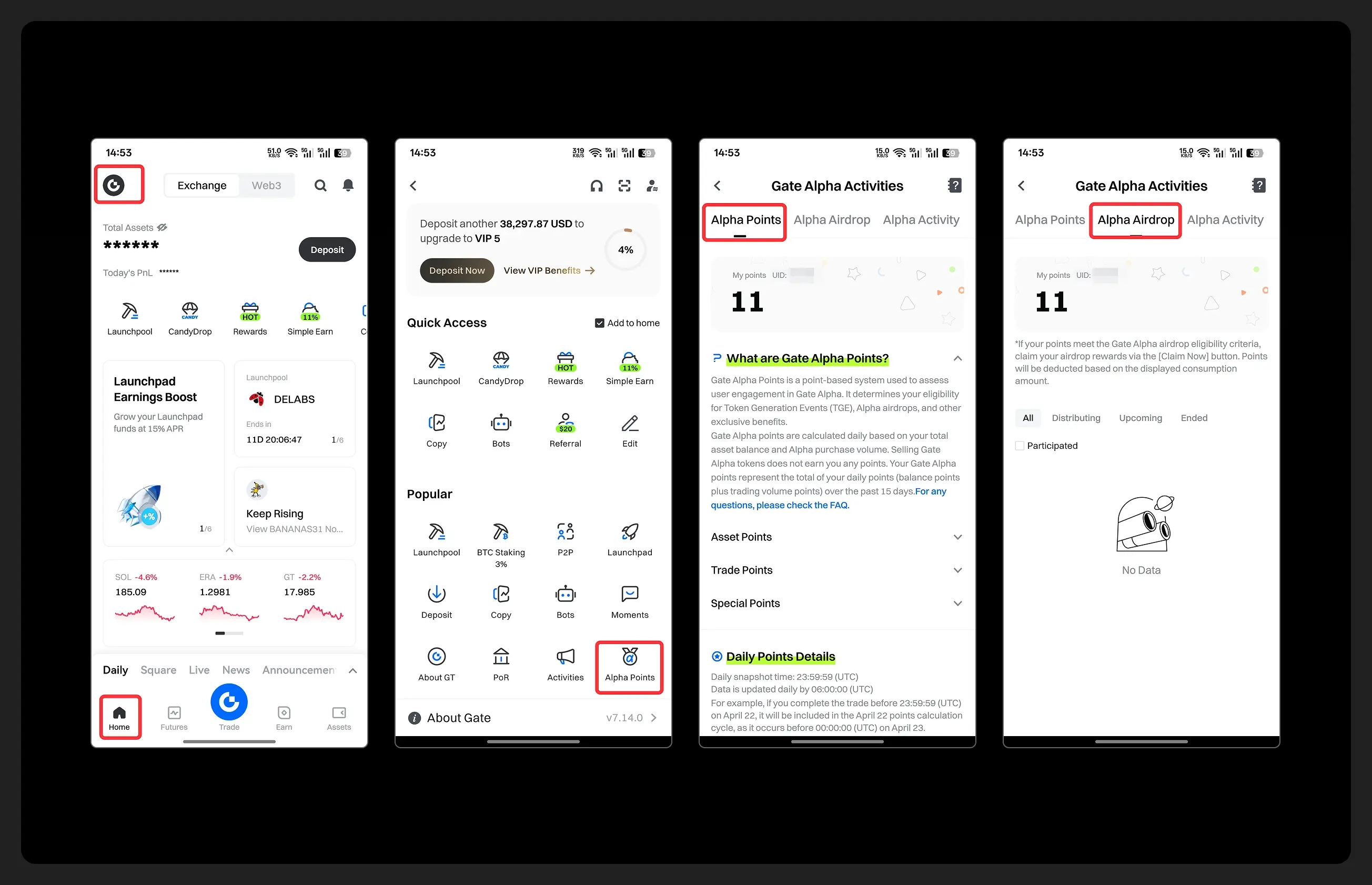
- Gate Futures Trading Incentive Program is Live! Zero Barries to Share 50,000 ERA
Start trading and earn rewards — the more you trade, the more you earn!
New users enjoy a 20% bonus!
Join now:https://www.gate.com/campaigns/1692?pid=X&ch=NGhnNGTf
Event details: https://www.gate.com/announcements/article/46429
- Hey Square fam! How many Alpha points have you racked up lately?
Did you get your airdrop? We’ve also got extra perks for you on Gate Square!
🎁 Show off your Alpha points gains, and you’ll get a shot at a $200U Mystery Box reward!
🥇 1 user with the highest points screenshot → $100U Mystery Box
✨ Top 5 sharers with quality posts → $20U Mystery Box each
📍【How to Join】
1️⃣ Make a post with the hashtag #ShowMyAlphaPoints#
2️⃣ Share a screenshot of your Alpha points, plus a one-liner: “I earned ____ with Gate Alpha. So worth it!”
👉 Bonus: Share your tips for earning points, redemption experienc
- 🎉 The #CandyDrop Futures Challenge is live — join now to share a 6 BTC prize pool!
📢 Post your futures trading experience on Gate Square with the event hashtag — $25 × 20 rewards are waiting!
🎁 $500 in futures trial vouchers up for grabs — 20 standout posts will win!
📅 Event Period: August 1, 2025, 15:00 – August 15, 2025, 19:00 (UTC+8)
👉 Event Link: https://www.gate.com/candy-drop/detail/BTC-98
Dare to trade. Dare to win.
Off-chain attack threats intensify as encryption tycoons face real-life kidnappings.
Off-chain Attacks: A New Threat in the Blockchain World
In the field of Blockchain, we often focus on technical risks such as on-chain attacks and smart contract vulnerabilities, but recent events remind us that threats have spread to the real world.
Recently, a cryptocurrency billionaire recounted a kidnapping attempt he experienced last year in court. The criminals tracked his movements through GPS, forged documents, and other means, and attempted to use a bag to suffocate him as he was going upstairs. Fortunately, the billionaire successfully fought back and escaped.
As the value of cryptocurrency assets continues to rise, real-world attacks targeting crypto users are becoming more frequent. This article will delve into the methods of such attacks, review typical cases, explore the underlying criminal networks, and provide some practical prevention suggestions.
The Concept of Wrench Attack
The term "wrench attack" originates from a web comic that depicts a scenario where an attacker, without sophisticated technology, is able to force a victim to surrender their password using only a $5 wrench. This type of attack does not rely on technical means, but instead employs physical methods such as threats, extortion, or even kidnapping to coerce the victim into giving up their password or assets.
Recent Typical Cases
Since the beginning of this year, there have been frequent kidnapping cases targeting crypto users, with victims including core project members, opinion leaders, and ordinary users.
In early May, French police successfully rescued the father of a cryptocurrency tycoon. The kidnappers demanded a huge ransom and cruelly severed the victim's fingers to pressure the family.
In January, a co-founder of a hardware wallet company and his wife were attacked at home by armed assailants. The kidnappers also used methods such as cutting off fingers and recording it, demanding a payment of 100 Bitcoins.
In early June, a man with dual French and Moroccan nationality was arrested in Tangier on suspicion of planning multiple kidnapping cases targeting French cryptocurrency entrepreneurs.
In New York, an Italian cryptocurrency investor was lured to a villa and subjected to three weeks of captivity and torture. The criminal gang used tools such as chainsaws and electric shock devices to threaten him, even hanging him from the top of a high-rise building, forcing him to hand over his wallet private keys.
In mid-May, the daughter and young grandson of a co-founder of a cryptocurrency trading platform were nearly forcibly taken away on the streets of Paris. Fortunately, passersby intervened in time, preventing a tragedy.
These cases indicate that, compared to on-chain attacks, real-world violent threats are more direct, efficient, and have a lower barrier to entry. It is worth noting that many of those involved in such crimes are younger, mostly aged 16 to 23, and possess basic knowledge of cryptocurrency.
In addition to publicly reported cases, the security team also discovered during the organization of user feedback that some users encountered control or coercion during offline transactions, resulting in asset losses.
In addition, there are some "non-violent coercion" incidents that have not escalated to physical violence, such as attackers threatening victims by掌握受害者的隐私信息. Although these situations have not caused direct harm, they have touched upon personal safety boundaries, and whether they should be classified as "wrench attacks" requires further discussion.
It is important to emphasize that the disclosed cases may only be the tip of the iceberg. Many victims choose to remain silent for various reasons, which also makes it difficult to accurately assess the true scale of off-chain attacks.
Crime Chain Analysis
According to the analysis by the research team at the University of Cambridge and several typical cases, we can summarize that the crime chain of a wrench attack usually includes the following key links:
Information Locking Attackers typically start with on-chain information, combining transaction behavior, tag data, etc., to make a preliminary assessment of the target asset scale. At the same time, social media information is also an important source of intelligence.
Realistic positioning and contact After determining the target identity, the attacker will attempt to obtain their real identity information, including residence, frequently visited locations, etc. Common methods include social media inducement, reverse lookup of public data, and reverse search of data leaks.
Violent Threats and Extortion Once the control target is established, attackers often use violent means to force them to hand over wallet private keys, recovery phrases, and other information. Common methods include physical harm, coercing transfers, and threatening relatives.
Money Laundering and Fund Transfer After obtaining the private key, attackers usually quickly transfer assets, using mixers, non-compliant exchanges, or OTC channels for money laundering and cashing out. Some attackers with a background in Blockchain technology will take complex fund flow paths to evade tracking.
Countermeasures
In the face of wrench attacks, traditional methods such as multi-signature wallets or distributed mnemonic phrases may not be practical in extreme cases. A more prudent strategy is "give and take, with controllable losses":
Conclusion
With the development of the cryptocurrency industry, KYC and AML systems play an important role in enhancing financial transparency and preventing illegal fund flows. However, there are still many challenges in the implementation process, especially in terms of data security and user privacy.
It is recommended to introduce a dynamic risk identification system based on the traditional KYC process to reduce unnecessary information collection and lower the risk of data breaches. At the same time, the platform can integrate professional anti-money laundering and tracking systems to enhance risk control capabilities from the source. Additionally, strengthening data security capabilities is equally important, which can be achieved through professional security testing services to comprehensively assess the exposure paths and risk points of sensitive data.