- Topic1/3
3k Popularity
24k Popularity
7k Popularity
5k Popularity
171k Popularity
- Pin
- Hey fam—did you join yesterday’s [Show Your Alpha Points] event? Still not sure how to post your screenshot? No worries, here’s a super easy guide to help you win your share of the $200 mystery box prize!
📸 posting guide:
1️⃣ Open app and tap your [Avatar] on the homepage
2️⃣ Go to [Alpha Points] in the sidebar
3️⃣ You’ll see your latest points and airdrop status on this page!
👇 Step-by-step images attached—save it for later so you can post anytime!
🎁 Post your screenshot now with #ShowMyAlphaPoints# for a chance to win a share of $200 in prizes!
⚡ Airdrop reminder: Gate Alpha ES airdrop is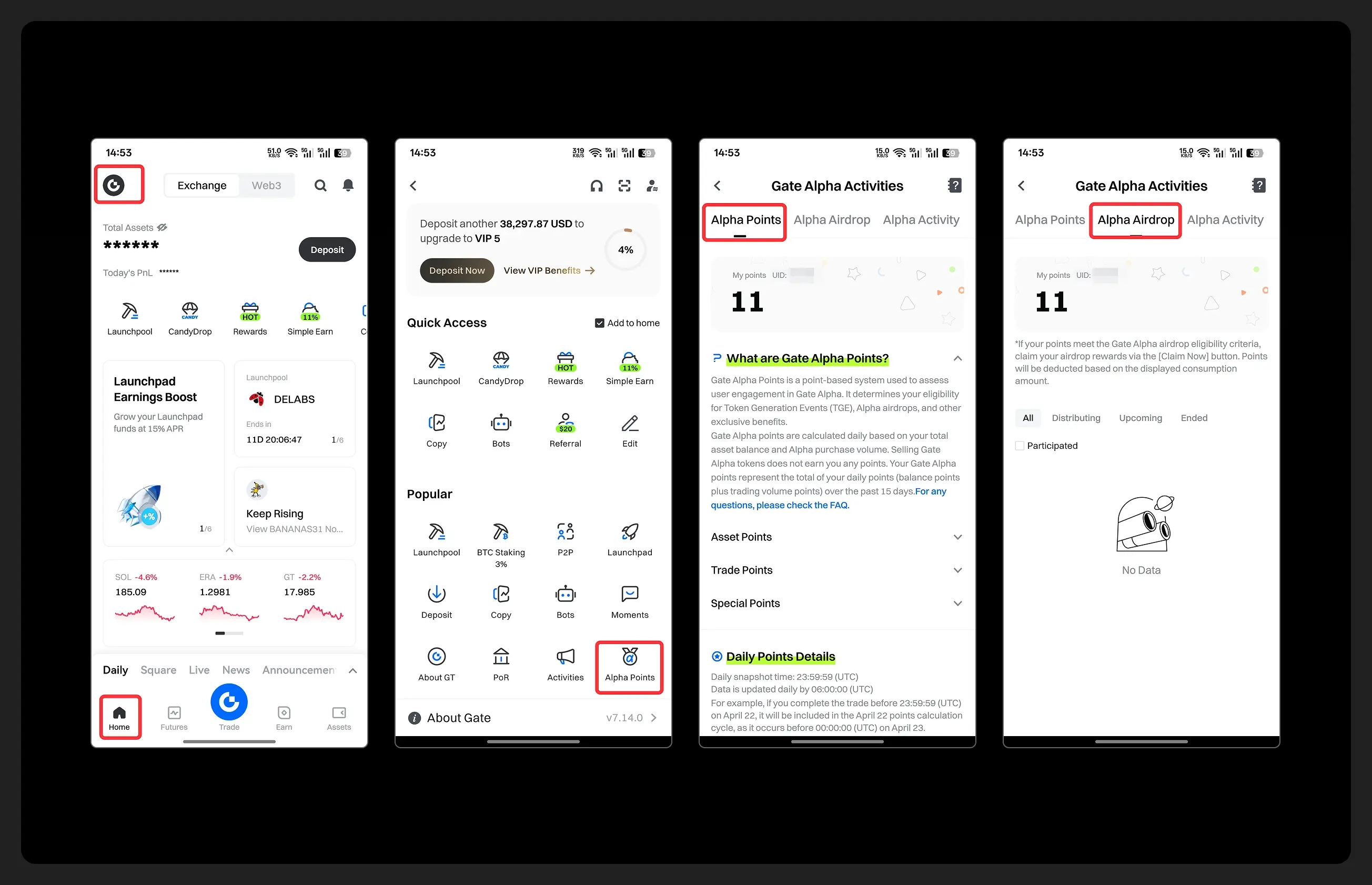
- Gate Futures Trading Incentive Program is Live! Zero Barries to Share 50,000 ERA
Start trading and earn rewards — the more you trade, the more you earn!
New users enjoy a 20% bonus!
Join now:https://www.gate.com/campaigns/1692?pid=X&ch=NGhnNGTf
Event details: https://www.gate.com/announcements/article/46429
- Hey Square fam! How many Alpha points have you racked up lately?
Did you get your airdrop? We’ve also got extra perks for you on Gate Square!
🎁 Show off your Alpha points gains, and you’ll get a shot at a $200U Mystery Box reward!
🥇 1 user with the highest points screenshot → $100U Mystery Box
✨ Top 5 sharers with quality posts → $20U Mystery Box each
📍【How to Join】
1️⃣ Make a post with the hashtag #ShowMyAlphaPoints#
2️⃣ Share a screenshot of your Alpha points, plus a one-liner: “I earned ____ with Gate Alpha. So worth it!”
👉 Bonus: Share your tips for earning points, redemption experienc
- 🎉 The #CandyDrop Futures Challenge is live — join now to share a 6 BTC prize pool!
📢 Post your futures trading experience on Gate Square with the event hashtag — $25 × 20 rewards are waiting!
🎁 $500 in futures trial vouchers up for grabs — 20 standout posts will win!
📅 Event Period: August 1, 2025, 15:00 – August 15, 2025, 19:00 (UTC+8)
👉 Event Link: https://www.gate.com/candy-drop/detail/BTC-98
Dare to trade. Dare to win.
Adapter signatures drive Bitcoin Layer 2 cross-chain atomic swap innovations
Adapter Signatures and Their Application in Cross-Chain Atomic Swaps
With the rapid development of Bitcoin Layer 2 scaling solutions, the frequency of cross-chain asset transfers between Bitcoin and Layer 2 networks has significantly increased. This trend is driven by the higher scalability, lower transaction fees, and high throughput offered by Layer 2 technology. These advancements facilitate more efficient and cost-effective transactions, thereby promoting broader adoption and integration of Bitcoin in various applications. As a result, interoperability between Bitcoin and Layer 2 networks is becoming a key component of the cryptocurrency ecosystem, driving innovation and providing users with more diverse and powerful financial tools.
There are three typical solutions for cross-chain transactions between Bitcoin and Layer 2, namely centralized cross-chain transactions, BitVM cross-chain bridge, and cross-chain atomic swaps. These three technologies differ in trust assumptions, security, convenience, transaction limits, etc., and can meet different application needs.
The advantages of centralized cross-chain trading lie in its speed and the relatively easy matching process, as centralized institutions can quickly confirm and process transactions. However, the security of this method completely relies on the reliability and reputation of the centralized institution. If the centralized institution encounters technical failures, malicious attacks, or defaults, users' funds face a higher risk. Furthermore, centralized cross-chain trading may also leak user privacy, requiring users to carefully consider this method when choosing it.
The BitVM cross-chain bridge technology is relatively complex. This technology introduces an optimistic challenge mechanism, making it relatively complicated. Additionally, the optimistic challenge mechanism involves a large number of challenge and response transactions, resulting in higher transaction fees. Therefore, the BitVM cross-chain bridge is only suitable for very large transactions and is used infrequently.
Cross-chain atomic swaps are a type of contract that enables decentralized cryptocurrency trading. Atomic swaps must involve two parties, and no third party can interrupt or interfere with the swapping process. This means that the technology is decentralized, censorship-resistant, offers good privacy protection, and allows for high-frequency cross-chain trading, making it widely applicable in decentralized exchanges.
The cross-chain atomic swap technology mainly includes hash time locks and adapter signatures. The cross-chain atomic swap based on the hash time lock ( HTLC ) has privacy leakage issues. The cross-chain atomic swap based on adapter signatures has three advantages: it replaces on-chain scripts, reduces on-chain space usage, and transactions cannot be linked, achieving privacy protection.
This article introduces the principles of Schnorr/ECDSA adapter signatures and cross-chain atomic swaps. It analyzes the security issues of random numbers present in adapter signatures and the system heterogeneity and algorithm heterogeneity issues in cross-chain scenarios, providing solutions. Finally, it extends the application of adapter signatures to achieve non-interactive digital asset custody.
Adapter signature and cross-chain atomic swap
Schnorr and ECDSA adapter signatures can be used to implement cross-chain atomic swaps. The basic principles of both schemes are similar, as they achieve atomic swaps by embedding secret values in the signatures.
Issues and Solutions
The adapter signature has security issues related to random number leakage and reuse. The solution is to use the RFC 6979 specification to generate deterministic random numbers.
In cross-chain scenarios, the system heterogeneity between the UTXO model and the account model can pose challenges. The solution is to implement exchange logic using smart contracts on the account model side.
For inter-system exchanges using the same curve but different signature algorithms, the adapter signature scheme is secure. However, for systems using different curves, the adapter signature cannot be used directly.
digital asset custody application
Adapter signatures can be used to implement non-interactive digital asset custody. The custodian does not need to participate in the initialization process and only needs to release the secret when necessary. This solution is more flexible than traditional multi-signatures and avoids the complex key generation process.
Verifiable encryption is the key technology to implement this custodial solution. Currently, there are two verifiable encryption schemes based on Secp256k1: Purify and Juggling.
Summary
The adapter signature provides a privacy-preserving solution for cross-chain atomic swaps. Reasonable design can overcome challenges such as random number security and system heterogeneity. Future exploration can further extend to applications in more complex scenarios, such as multi-party asset custody.