- Topic1/3
20k Popularity
36k Popularity
21k Popularity
6k Popularity
174k Popularity
- Pin
- Hey fam—did you join yesterday’s [Show Your Alpha Points] event? Still not sure how to post your screenshot? No worries, here’s a super easy guide to help you win your share of the $200 mystery box prize!
📸 posting guide:
1️⃣ Open app and tap your [Avatar] on the homepage
2️⃣ Go to [Alpha Points] in the sidebar
3️⃣ You’ll see your latest points and airdrop status on this page!
👇 Step-by-step images attached—save it for later so you can post anytime!
🎁 Post your screenshot now with #ShowMyAlphaPoints# for a chance to win a share of $200 in prizes!
⚡ Airdrop reminder: Gate Alpha ES airdrop is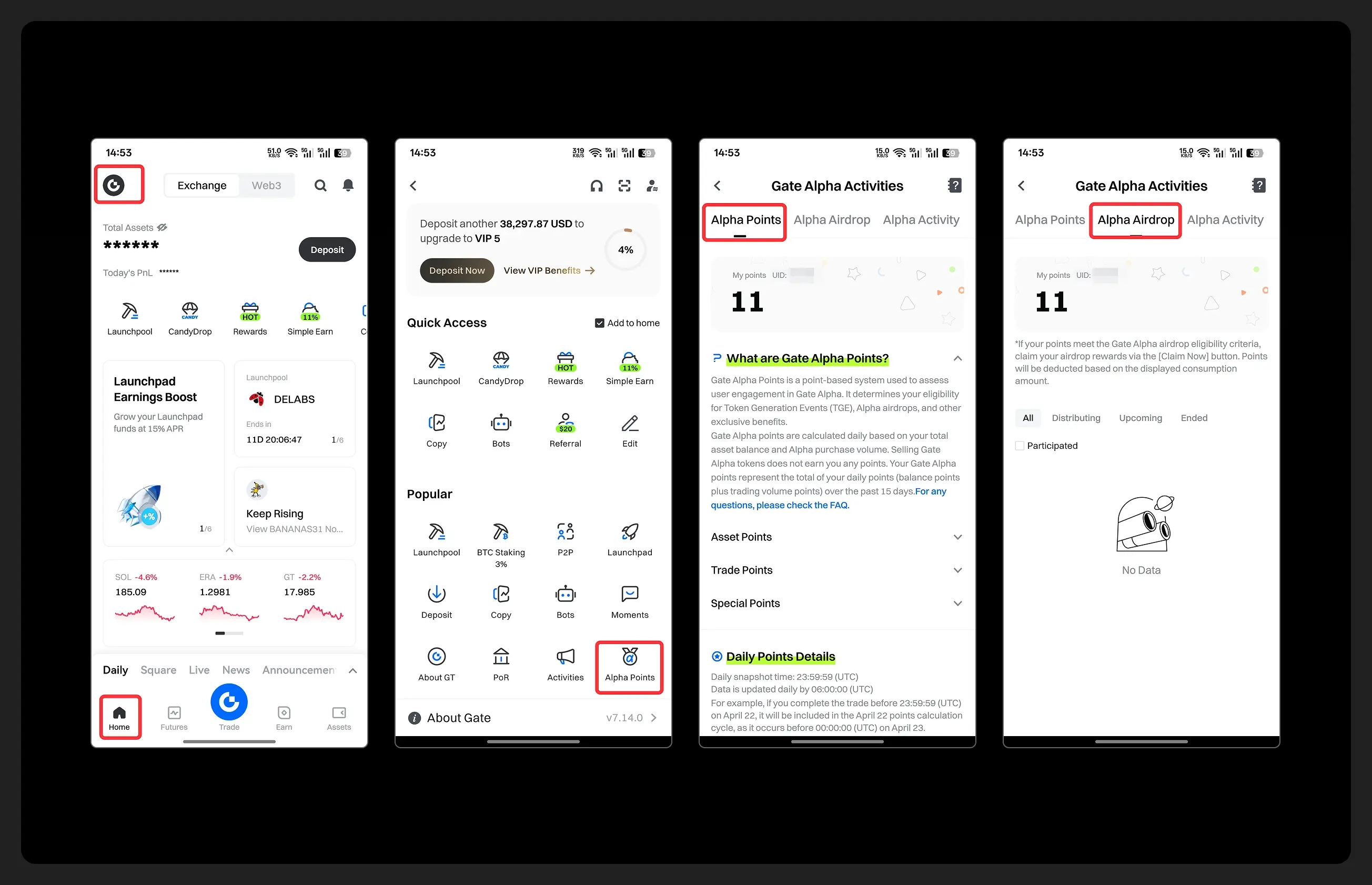
- Gate Futures Trading Incentive Program is Live! Zero Barries to Share 50,000 ERA
Start trading and earn rewards — the more you trade, the more you earn!
New users enjoy a 20% bonus!
Join now:https://www.gate.com/campaigns/1692?pid=X&ch=NGhnNGTf
Event details: https://www.gate.com/announcements/article/46429
- Hey Square fam! How many Alpha points have you racked up lately?
Did you get your airdrop? We’ve also got extra perks for you on Gate Square!
🎁 Show off your Alpha points gains, and you’ll get a shot at a $200U Mystery Box reward!
🥇 1 user with the highest points screenshot → $100U Mystery Box
✨ Top 5 sharers with quality posts → $20U Mystery Box each
📍【How to Join】
1️⃣ Make a post with the hashtag #ShowMyAlphaPoints#
2️⃣ Share a screenshot of your Alpha points, plus a one-liner: “I earned ____ with Gate Alpha. So worth it!”
👉 Bonus: Share your tips for earning points, redemption experienc
- 🎉 The #CandyDrop Futures Challenge is live — join now to share a 6 BTC prize pool!
📢 Post your futures trading experience on Gate Square with the event hashtag — $25 × 20 rewards are waiting!
🎁 $500 in futures trial vouchers up for grabs — 20 standout posts will win!
📅 Event Period: August 1, 2025, 15:00 – August 15, 2025, 19:00 (UTC+8)
👉 Event Link: https://www.gate.com/candy-drop/detail/BTC-98
Dare to trade. Dare to win.
NEST Oracle Machine Faces Risk Analysis of Mining Pool Rejection Attack
Analysis of Mining Pool Refusal to Package Attack Faced by NEST Oracle Machine
The NEST distributed Oracle Machine aims to enhance the reliability of price data and the security of the system by allowing more on-chain users to participate in the price determination process. To prevent malicious quoting, NEST has designed a quoting-eating order verification mechanism that allows verifiers to trade based on the quote and propose corrections.
However, the effectiveness of this mechanism relies on the timely appearance of market orders and new quote trades in new blocks. With the emergence of Mining Pools, the monopoly on transaction packaging rights has become a potential issue. Large Mining Pools may selectively package transactions that are beneficial to themselves or have higher fees, rather than the transactions that are broadcasted first.
This situation may cause the NEST Oracle Machine to be unable to verify new quotes in a timely manner, ultimately resulting in erroneous price data. Certain Mining Pools may take advantage of this opportunity for arbitrage, threatening the security of the entire DeFi ecosystem.
The attack process is roughly as follows:
Malicious Mining Pool pre-stocks cryptocurrency for arbitrage.
Submit a quote to NEST that differs significantly from the actual market price.
During the verification period, other Mining Pools face the choice of whether to package the corrected transaction.
Each Mining Pool makes game-theoretic decisions based on its own computing power and potential earnings.
If enough Mining Pools choose not to package corrected transactions, erroneous quotes may be confirmed.
Malicious mining pools exploit erroneous prices for arbitrage.
This attack utilizes the concept of Nash equilibrium in game theory. Each Mining Pool will weigh the benefits of immediately correcting the quote (a) against the benefits of waiting for the incorrect quote to be confirmed and then arbitraging (b). Typically, b > a, but the probability of obtaining the benefit is proportional to the Mining Pool's hash power.
Ultimately, the Mining Pool will make decisions based on its own computing power ratio and the proportional relationship between the two types of income. This phenomenon not only affects the NEST Oracle Machine but also poses a challenge to the entire decentralized concept of blockchain.
How to effectively solve the problems caused by the centralization of Mining Pools is an unavoidable important topic in the process of blockchain moving towards true decentralization.