- Topic1/3
20k Popularity
36k Popularity
21k Popularity
6k Popularity
42k Popularity
- Pin
- Hey fam—did you join yesterday’s [Show Your Alpha Points] event? Still not sure how to post your screenshot? No worries, here’s a super easy guide to help you win your share of the $200 mystery box prize!
📸 posting guide:
1️⃣ Open app and tap your [Avatar] on the homepage
2️⃣ Go to [Alpha Points] in the sidebar
3️⃣ You’ll see your latest points and airdrop status on this page!
👇 Step-by-step images attached—save it for later so you can post anytime!
🎁 Post your screenshot now with #ShowMyAlphaPoints# for a chance to win a share of $200 in prizes!
⚡ Airdrop reminder: Gate Alpha ES airdrop is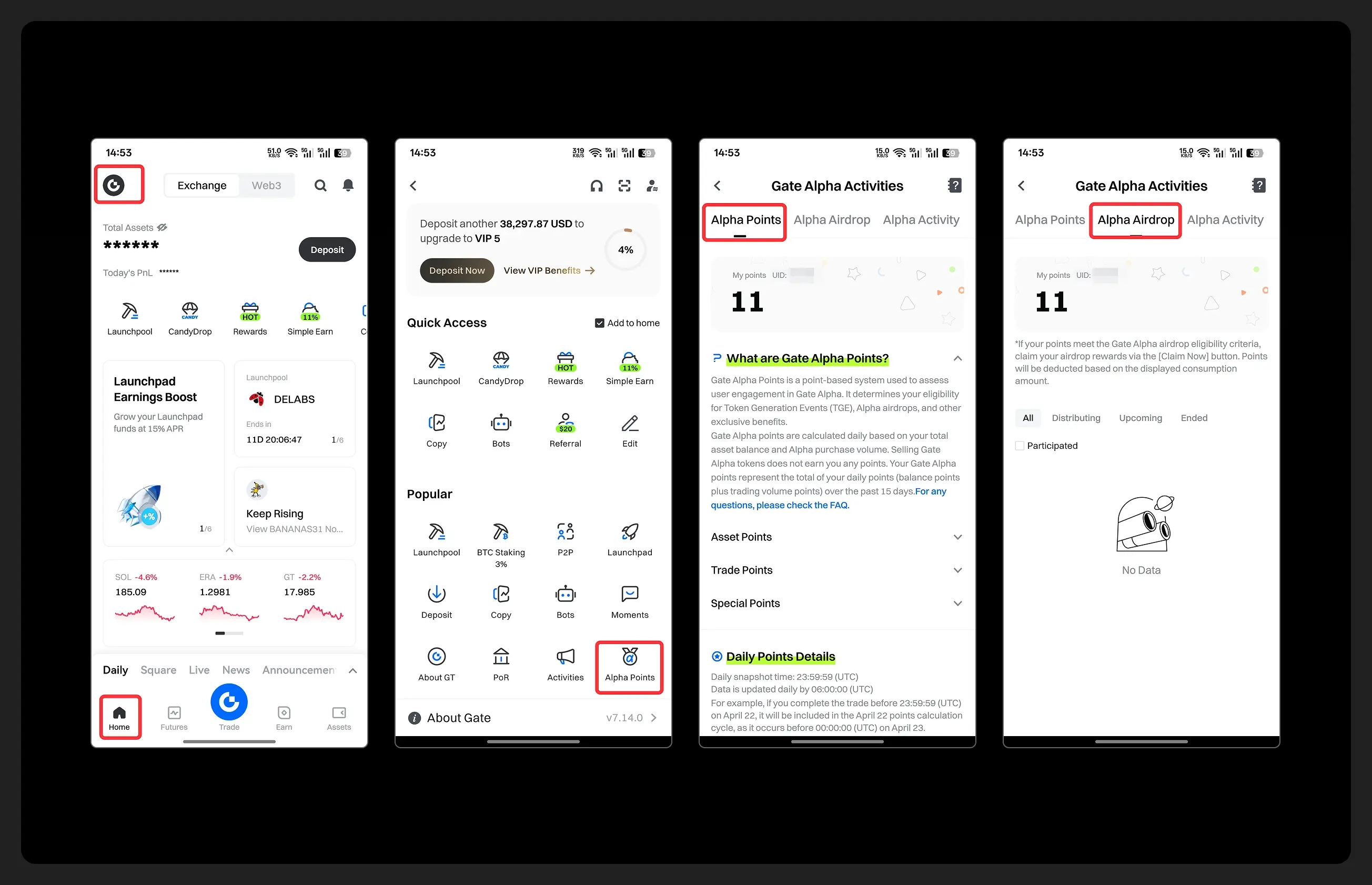
- Gate Futures Trading Incentive Program is Live! Zero Barries to Share 50,000 ERA
Start trading and earn rewards — the more you trade, the more you earn!
New users enjoy a 20% bonus!
Join now:https://www.gate.com/campaigns/1692?pid=X&ch=NGhnNGTf
Event details: https://www.gate.com/announcements/article/46429
- Hey Square fam! How many Alpha points have you racked up lately?
Did you get your airdrop? We’ve also got extra perks for you on Gate Square!
🎁 Show off your Alpha points gains, and you’ll get a shot at a $200U Mystery Box reward!
🥇 1 user with the highest points screenshot → $100U Mystery Box
✨ Top 5 sharers with quality posts → $20U Mystery Box each
📍【How to Join】
1️⃣ Make a post with the hashtag #ShowMyAlphaPoints#
2️⃣ Share a screenshot of your Alpha points, plus a one-liner: “I earned ____ with Gate Alpha. So worth it!”
👉 Bonus: Share your tips for earning points, redemption experienc
- 🎉 The #CandyDrop Futures Challenge is live — join now to share a 6 BTC prize pool!
📢 Post your futures trading experience on Gate Square with the event hashtag — $25 × 20 rewards are waiting!
🎁 $500 in futures trial vouchers up for grabs — 20 standout posts will win!
📅 Event Period: August 1, 2025, 15:00 – August 15, 2025, 19:00 (UTC+8)
👉 Event Link: https://www.gate.com/candy-drop/detail/BTC-98
Dare to trade. Dare to win.
zkTLS: The Key Bridge Connecting Web2 and Web3
The Divide Between Web3 and Web2: Exploring the Potential of zkTLS
Despite the fact that Web3 technology has developed powerful tools and infrastructure, the daily lives of ordinary internet users still primarily take place in a Web2 environment.
Current Situation Analysis
The cryptocurrency industry has made significant progress. Layer 2 scaling solutions have been implemented, zkVMs technology has emerged, and even cryptocurrency ETFs have received regulatory approval. However, for most people, the blockchain space still feels distant - it exists more in news reports than in practical applications.
Challenge location
The core of the problem lies not in the technology itself, but in the areas it currently cannot reach: our digital lives. Although Web3 has built powerful tools and infrastructure, the everyday activities of ordinary internet users still take place in Web2 environments - they browse, trade, and socialize on centralized platforms that control user data.
Mainstream adoption of Web3 still faces challenges before we can connect these two worlds in a trustless and privacy-protecting manner.
The reasons why Web3 has not been able to break through
Our online interactions cover multiple areas - including banking, social media, streaming platforms, and government portals. But all of these activities take place within a strictly controlled ecosystem. Our digital identities are scattered across various platforms, each holding a part of our lives: there are bank statements here, passport scans over there, and work experiences on professional networking platforms.
This fragmentation has brought about two fundamental issues:
These issues are reflected in the frictions we face every day. For example, when proof of income is required, a complete bank statement may need to be provided. When address verification is needed, an entire utility bill may need to be uploaded. These systems assume that complete transparency is the only way to build trust, due to a lack of infrastructure for selective, verifiable disclosures.
Web3 promises to empower users with control, but so far it has not fully delivered on that promise - at least not for everyday data derived from Web2.
The Missing Key: Verifiable Web2 Data
This is the real bottleneck: how to enable Web3 applications to leverage the data we have already generated - while not compromising user privacy or introducing new trusted intermediaries.
There are two key challenges:
Some oracle providers have addressed certain verifiability issues, particularly for public data such as asset prices or weather conditions. However, personal and user-specific data - such as financial records, qualifications, and identity credentials - require different approaches. These data points exist within encrypted channels after logging in, and they are not designed to be extracted or shared.
This is where zkTLS comes into play.
Introduction to zkTLS
Most of the internet runs on TLS (Transport Layer Security) - the encryption protocol that underpins HTTPS. It protects about 95% of web traffic. When a user visits a website, TLS ensures that the communication is encrypted and has not been tampered with.
zkTLS (Zero-Knowledge TLS) builds on this foundation to create some entirely new functionalities: it allows users to extract and prove specific facts from Web2 data streams without revealing the full content or trusting a third party.
This unlocks two key capabilities:
Its working principle is briefly described as follows:
This avoids the need to expose data to third parties or rely on centralized servers to prove the data. Instead, trust is embedded within the cryptographic proof itself.
This is not just theory. The implementation of zkTLS has been tested and deployed in consumer and DeFi use cases, indicating that verifiable Web2 data will become the default input for Web3 applications.
Practical Applications of zkTLS
zkTLS not only optimizes data processing - it also redefines the boundaries between Web2 and Web3. By implementing trust minimization and private access to off-chain data, it allows applications to integrate real-world context without compromising privacy or decentralization.
The following are its current applications in different fields.
Financial Services
Due to the lack of reliable identity and on-chain financial data, most decentralized finance protocols still rely on over-collateralization. zkTLS enables the verification of income, cash flow, or account history without exposing sensitive documents.
These systems expand the channels for capital acquisition, bring credit value on-chain, and establish a compliant bridge between traditional finance and cryptocurrency.
Consumer Platform
In Web2, access to digital goods, subscriptions, and purchase history is locked behind centralized APIs. zkTLS makes this data portable and provable - without needing to request permission from the platform.
Now imagine proving that you have a music streaming subscription - or a luxury brand purchase - without revealing your full account. This is the power of zkTLS.
Identity and Reputation
Today's digital identity is fragmented and overly exposed. Proving identity often means sharing too much information. zkTLS changes this by allowing selective disclosure from trusted sources.
Now imagine someone building a Web3 version of a ride-sharing or food delivery platform. Drivers show up with zkTLS-verified credentials - no onboarding friction, no need to rebuild reputation.
Social and Content
The content we watch, play with, and interact with says a lot - but this data is trapped within the platform. zkTLS unlocks this data, making participation portable and programmable.
This unlocks the next wave of the attention market and participation-driven rewards - ultimately cross-platform portable.
Impact and Behavior
Behavior systems - whether for fitness, sustainability, or rewards - typically require private and hard-to-verify data. zkTLS makes it possible to prove actions without surveillance.
Other applications are exploring the use of zkTLS to prove public transportation usage, recycling, or participation in environmental projects - achieving a transparent and privacy-preserving incentive system.
With zkTLS, we can finally prove actions in the real world - without being surveilled.
Emerging Frontier
At the intersection of artificial intelligence, agents, and decentralized coordination, zkTLS provides critical infrastructure for proof and trust.
As agents and AI become more autonomous, zkTLS anchors them in fact.
From Certificate to Ownership
zkTLS not only makes Web2 data available in Web3 - it also makes it ownable. Credentials that were once isolated on platforms become portable, programmable, and privacy-preserving.
As more applications adopt zkTLS, we will see a compound effect: more verifiable data leads to more powerful applications, thereby giving users greater control - and more reasons to unlock data on their own terms.
This is not meant to replace existing systems. Rather, it aims to empower users with control over them - and to build a path of trust, privacy, and composability that expands together.
Future Outlook
If cryptographic technology wants to enter the mainstream, it needs to meet the needs of users - on the internet they are already using. zkTLS provides the foundation to achieve this goal.